ThoughtSpot can use Security Assertion Markup Language (SAML) to authenticate
users. You can set up SAML through the shell on the ThoughtSpot instance using a
tscli based configurator, or through the Admin Console.
Before configuring SAML, you need this information:
- Domain name for ThoughtSpot service (E.g. -
thoughtspot.ts-customer.com). - Port of the server where your ThoughtSpot instance is running (E.g. -
443). - Protocol, or the authentication mechanism for ThoughtSpot (E.g. -
httporhttps) - Unique service name that is used as the unique key by IDP to identify the client (E.g. -
urn:thoughtspot:callosum:saml) - Allowed skew time, which is the time after authentication response is rejected and sent back from the IDP.
86400is a popular choice. - The absolute path to identity provider’s metadata file. Typically called
idp-meta.xmlor similar. This is needed so that the configuration persists over upgrades. Best to set it up on persistent/HA storage (NAS volumes) else in the same absolute path on all nodes in the cluster. - This configurator also checks with the user if internal authentication needs to be set or not. This internal authentication mechanism is used to authenticate
tsadminand other ThoughtSpot local users. Set it to true by default to let local system/admin users in via the frontend.
Configure SAML using tscli
Use this procedure to set up SAML on ThoughtSpot for user authentication. Note that this configuration persists across software updates, so you do not have to reapply it if you update to a newer release of ThoughtSpot.
- Log in to the Linux shell using SSH.
-
Execute the command to launch the interactive SAML configuration:
tscli saml configure - Complete the configurator prompts with the information you gathered above.
- When the configuration is complete, open a Web browser and go to the ThoughtSpot login page. It should now show the Single Sign On option.
Configure SAML using the Admin Console
You can use ThoughtSpot’s integration with SAML for user authentication. By default, local authentication is enabled. You can also configure a SAML integration with an external Identity Provider (IdP), allowing your ThoughtSpot users to log in using one of the supported Identity Providers: Okta, Ping Identity, CA SiteMinder, or ADFS.
You can configure the SAML integration through the Admin Console.
Navigate to the Admin Console by clicking on the Admin tab from the top navigation bar. Select SAML from the side navigation bar that appears.
Click the Configure button in the middle of the screen.
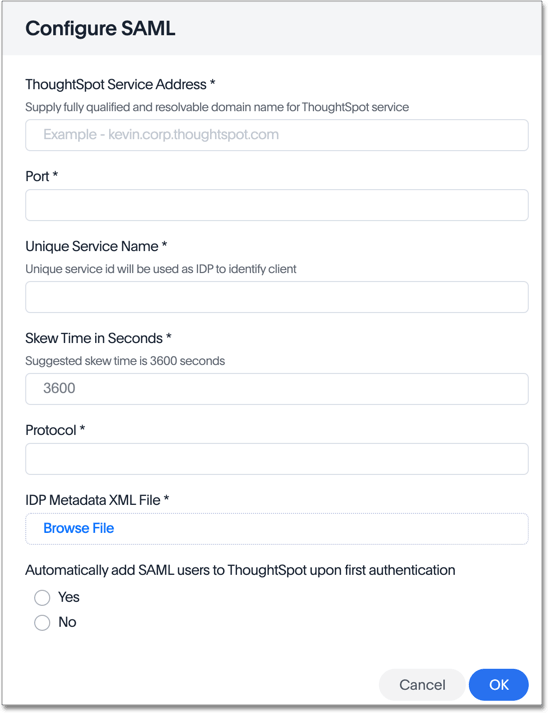
Fill in the following parameters:
- ThoughtSpot Service Address: A fully qualified and resolvable domain name for the ThoughtSpot service. For example, thoughtspot.thoughtspot-customer.com.
- Port: Port of the server where your ThoughtSpot instance is running. For example, port
443. - Unique Service Name: The unique key used by your Identity Provider to identify the client. For example, urn:thoughtspot:callosum:saml.
- Skew Time in Seconds: The allowed skew time, after which the authentication response is rejected and sent back from the IDP. 86400 is a popular choice. The default is 3600.
- Protocol: The authentication mechanism for ThoughtSpot. For example,
httporhttps. - IDP Metadata XML File: The absolute path to your Identity Provider’s metadata file. This file is provided by your IDP. You need this file so that the configuration persists over upgrades. It is a best practice to set it up on persistent/HA storage (NAS volumes) or in the same absolute path on all nodes in the cluster. For example, idp-meta.xml.
- Automatically add SAML users to ThoughtSpot upon first authentication: Choose whether or not to add SAML users to ThoughtSpot when they first authenticate. If you choose ‘yes’, then new users will be automatically created in ThoughtSpot upon first successful SSO login. If you choose ‘no’, then SAML users will not be added in ThoughtSpot upon first successful SSO login. Instead, you must add users manually.
After you fill in all parameters, click OK.